Note
You are viewing the documentation for an older release of Interworx (6.x). To see documentation for the current generally available release of Interworx, click here: 7.13.
Firewall¶
Introduction:¶
What is a firewall?¶
A firewall is a device that analyzes incoming and outgoing network traffic and decides whether it should be allowed through or not based on a set of rules as determined by the user.
APF¶
InterWorx uses APF, which is an acronym for Advanced Policy Firewall. APF is a policy based iptables-based firewall. APF provides an easy to use front end for iptables.
Use¶
Firewall Control¶
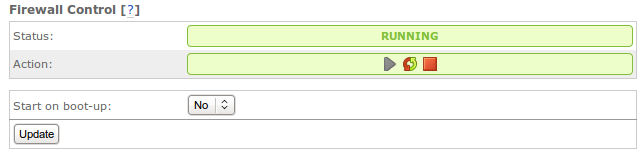
Service Control for FireWall¶
In the figure above, you can see the box allows the user to start, restart, and stop APF via gui. 1
Start on boot-up¶
Toggles whether or not you wish that InterWorx starts APF when the system reboots.
Firewall Information¶
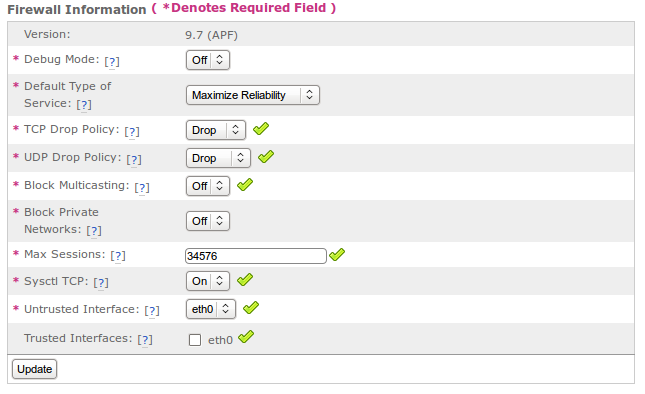
This section displays and edits configuration information for APF (note: the default configuration is best for most users)¶
Debug mode¶
When debug mode is enabled, all firewall rules are flushed every 5 minutes to prevent being locked out of the server due to a firewall misconfiguration.
Default Type of Service¶
Defines the default type of service (Maximize Reliaibility, Maximize Throughput, Minimize Delay).
TCP Drop Policy¶
Defines how to handle TCP packet filtering. “Reset” sends a tcp-reset message, “Drop” silently drops the packet, “Reject” rejects the packet.
UDP Drop Policy¶
Defines how to handle UDP packet filtering. “Reset” sends an icmp-port-unreachable message, “Drop” will silently drop the packet, “Reject” will reject the packet, and “Prohibit” will send an icmp-host-prohibited message.
Block Multicasting¶
Defines if the firewall should block multicast traffic.
Block Private Networks¶
Defines if the firewall should block all private ipv4 addresses (reserved address space, generally unroutable on the internet). If the server sites behind a NAT or other routing setup that would make use of private addressing, leave this option “Off”.
Max Sessions¶
Defines the maximum number of connection tracking entries that can be handled by the firewall simultaneously.
Sysctl TCP¶
Enables or Disables sysctl hook changes to harden the kernel from certain network-based attacks.
Untrusted Interface¶
All traffic on defined interface will be subject to all firewall rules. This should be your internet exposed interface.
Trusted Interfaces¶
All traffic on defined interface(s) will bypass all firewall rules.
Click ’Update’ to commit changes.
Global IP Access Control¶
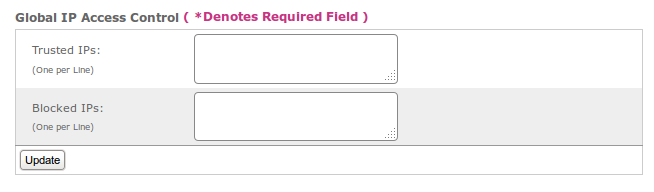
Gloal IP Access Control¶
Trusted IPs¶
Add one trusted IP per line to allow all traffic to and from that address.
Blocked IPs¶
Add one blocked IP to prevent all traffic to and from that address.
Port Access¶
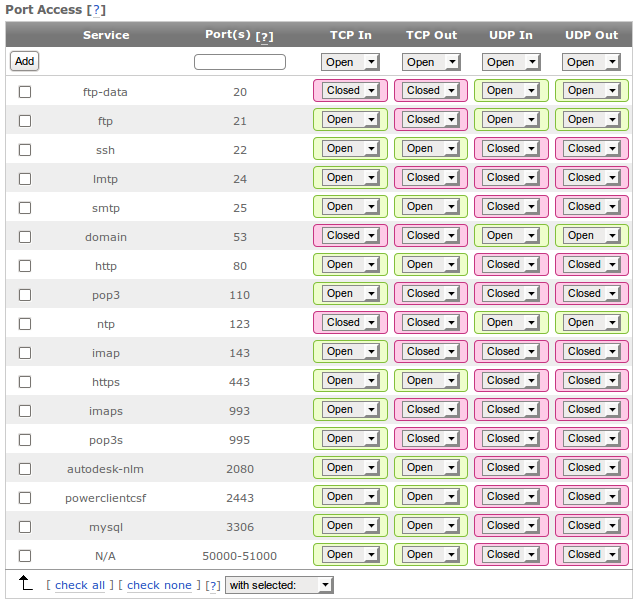
Port Access Table¶
This table is used to open and close specific ports on your firewall. The port rules defined here will apply to all incoming IPs that are not defined in either the Trusted or Blocked IP lists. (Note: The default configuration is best for most users.)
Note
Note: Port 2443 must be open for the control panel to function correctly.
- 1
The panel will automatically indicate whether or not APF is running.